In this part, we will discuss types of threat intelligence and several use cases in real-world scenarios.
Types of Threat Intelligence
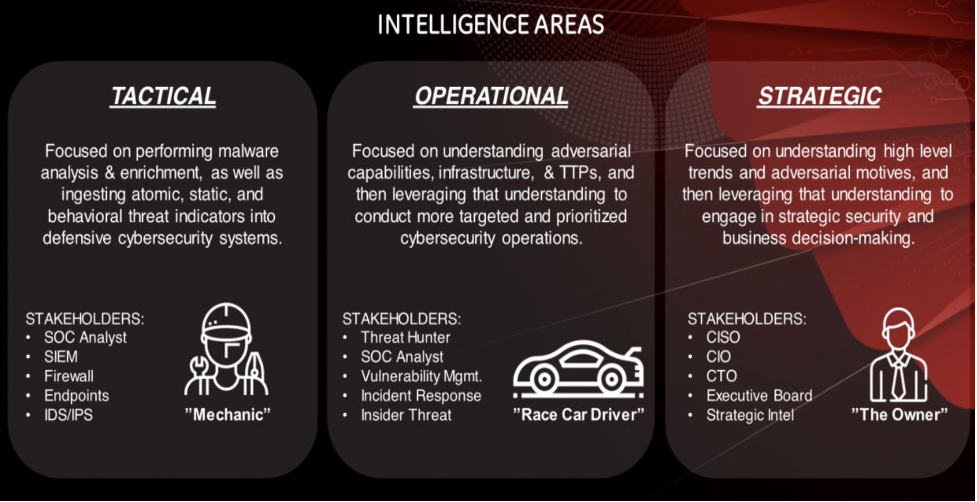
There are 3 types of threat intelligence:
- Tactical—Focuses on analysis of threat actors for a more technically sound audiences
- Operational—Technical details i.e. TTPs about specific attacks and campaigns.
- Strategic—High-level trends typically meant for a non-technical audience.
Tactical Threat Intelligence
Tactical intelligence is focused on the immediate future, obtain a broader perspective of threats, is technical in nature, and identifies singular threats. Singular threats are things like bad IP addresses, URLs, file hashes, and malicious domain names. Tactical intelligence is used by personnel who are directly working or involved in the defense team of an organization.
This intelligence is the easiest to generate as it is always automated and can be found via open source or free data feeds. However, you must be aware of the authenticity of the data source because if it is not timely or of high fidelity it may give you false-positive results.
Tactical threat intelligence is very useful to suggest improvements in the existing security controls and speed up incident response. Most of the issues addressed by tactical intelligence are unique to your organization.
Operational Threat Intelligence
Operational intelligence gives insight into cyberattacks, events, or campaigns. This specialized insight gives the incident response team a better understanding of the nature, extent, and timing of an attack. In short, operational threat intelligence tracks the ‘who’, ‘why’, and ‘how’ behind every attack.
Operational intelligence consumes more resources compared to tactical intelligence but it has a longer useful life as cybercriminals can’t change their TTPs as fast as they can change their tools or infrastructure. It is noted that machines alone can’t create viable operational threat intelligence. Human intelligence is inevitable to convert data into a readily usable format. However, machines can definitely reduce human efforts in this context.
Professionals working in Security Operations Center (SOC) find operational intelligence most useful. Several cybersecurity disciplines like threat monitoring, vulnerability management, and incident response are some of the biggest consumers of operational intelligence.
Strategic Threat Intelligence
Strategic intelligence gives you a broad overview of the threat landscape. It helps executives and decision-makers to make informed decisions thus the nature & content of the intelligence is less technical in the form of reports or briefings.
Common sources of information for strategic intelligence include the following:
- News from local & national media
- Industry-specific publications
- Policy documents from both government & non-government organizations.
- Research reports, white papers, and security organization’s published papers.
Executives and the board of directors can determine an effective cybersecurity investment after understanding the strategic intelligence. This intelligence is the hardest form to generate as it considers global events, foreign policies, and other international movements.
Although the final report is non-technical strategic intelligence still requires intense human effort including data collection, analysis, research across multiple platforms, and deep research. At the same time, the team should have a thorough understanding of the world’s geopolitical situation as well as cybersecurity nuances.
Threat Intelligence Use Cases
Diverse use cases of threat intelligence have made it an essential resource for cross-functional teams across organizations. Here are some of the uses cases of threat intelligence.
Incident Response
The Head of the incident response team probably faces the highest level of stress as the rate of cyber incidents has climbed up steadily over the past 10-15 years. On top of that, a significant percentage of daily alerts turn out to be false positives. And when any genuine incident takes place the analysts must spend time to sort data and assess the problem.
Threat intelligence can ease the burden in several ways:
- Automatic identification and dismissal of false positives
- Comparing information from both internal and external sources
- Enriching alerts with real-time context
Security Operations
SOC teams deal with hundreds and thousands of alerts generated by the networks. Dealing with these attacks takes too long and often the team gets tired with ‘alert fatigue'. Threat intelligence can solve the problems by gathering information accurately & quickly, filtering out false alarms, and simplifying incident analysis.
Vulnerability Management
Effective vulnerability management means prioritize vulnerabilities based on actual risks. Despite the increasing number, it is evident by research that most threats target a small proportion of vulnerabilities. Moreover, threat actors are fast—it usually takes around 2 weeks starting from announcing the new vulnerability to exploiting the target.
Threat intelligence can help you to identify the actual risk—goes beyond CVE scoring by combining internal vulnerability and additional context about the TTPs of threat actors.
Fraud Prevention
For the safe keeping of your organization, you need to prevent fraudulent uses of your data or brand. Threat intelligence gathered from underground criminal networks provides you a good insight regarding the tactics of threat actors.
You can use threat intelligence to prevent payment fraud, compromised data, typosquatting and many other similar activities.
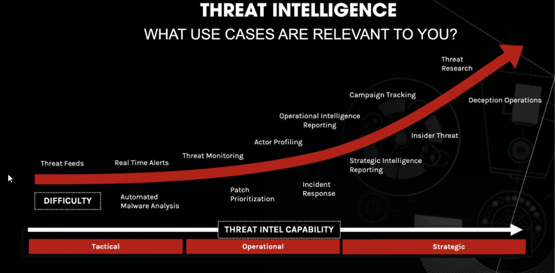
There are some other use cases as mentioned briefly in the below image:



 714-333-9620
714-333-9620