What is Threat Intelligence?
Digital technologies facilitate automation and greater connectivity in nearly every industry today. This is a great boon, undoubtedly. However, they have also brought risks in the form of cyberattacks. Threat intelligence can provide data-backed knowledge so that you can prevent or at least mitigate such attacks.
“Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and action-oriented advice about an existing or emerging menace or hazard to assets. This intelligence can be used to inform decisions regarding the subject’s response to that menace or hazard.” — Gartner
Importance of Threat Intelligence
The cybersecurity industry faces a multitude of challenges these days:
- Ever-increasing threat landscape from devious threat actors.
- Data flood with extraneous information
- False alarms across unconnected security systems due to unstructured data
- A severe shortage of skilled cybersecurity professionals.
The good news is, organizations have already started to realize the value of threat intelligence. Around 72% are planning to increase their threat intelligence budget in the upcoming months. Some other organizations are trying to incorporate threat data feeds into their existing network, IPS, firewalls and SIEMs. However, their data analysts may not have the right tools to get the full benefits from the insight.
Cyber threat intelligence, when applied correctly, can address all of the above issues. Solutions that are equipped with AI and ML can
- Process unstructured data from disparate sources to identify IoCs and the tactics, techniques and procedures (TTPs) of threat actors.
- Enable security teams to make better decisions by shedding light on the unknown.
- Empower business stakeholders i.e. CISOs, executive boards and CTOs to invest wisely, mitigate risk and take faster decisions in a more efficient way.
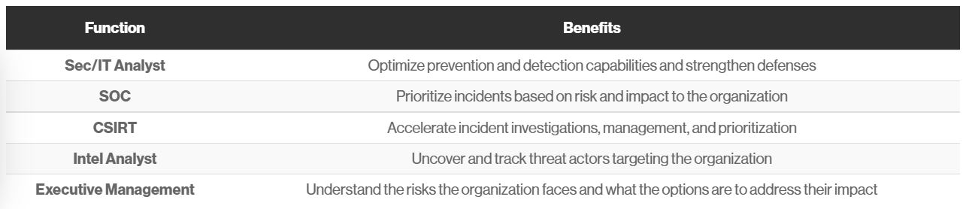
Who Benefits from Threat Intelligence?
Cyber threat intelligence is widely imagined to be the domain of elite analysts. It adds value across organizations of all sizes by helping process threat data to better understand the attackers, their motives and proactively gets ahead of the threat actor’s next move!
Threat intelligence provides several unique benefits to every member of a security team. Below is a chart of how it can benefit each security team member.
Lifecycle of Threat Intelligence
The goal of threat intelligence is to transform raw and unstructured data into structured outcomes for decision making. The intelligence cycle guides the cybersecurity team through the development and execution of an effective threat intelligence program.
The intelligence cycle sets a framework that facilitates teams to optimize their available resources thus responding effectively to the constantly evolving threat landscape. An effective intelligence program is iterative and becomes more refined over time.
There are 6 steps and we are going to explore them below:
- Requirements
Ask the right question! That’s the first step to producing actionable threat intelligence. The objectives of the intelligence should adhere to your organization’s core values. Besides, the taken decision should be time sensitive with a significant impact on the security outcome.
The guiding factor here is to determine the end-user who will get the ultimate benefit from the intelligence, the attackers’ motives and the attack surface.
- Collection
In this second step, the security team has to collect the information required to satisfy the above objectives and requirements. Your data source should be as wide as possible—encompassing internal ones like event logs, network & records of past incident responses and external ones like the dark web, the open web as well as technical sources.
Malicious IP addresses, IoCs, domains and file hashes are often considered as threat data. However, your security team must consider customers’ personal information, raw code from past sites, vulnerability information, text from news sources & social media as threat data.
- Processing
As soon as all raw and unstructured data have been collected the security team needs to sort it with metadata tags. Redundant information should be excluded to eliminate possibility of false positives or false negatives. Traditional methods of data organization include coded spreadsheets, decrypting files and translating information from foreign sources.
However, these days even small organizations collect tons of data from a multitude of internal & external sources. Likewise, it becomes difficult for human analysts to process such voluminous unstructured data to something digestible. Automated data collection and processing tools can serve the purpose in a better way.
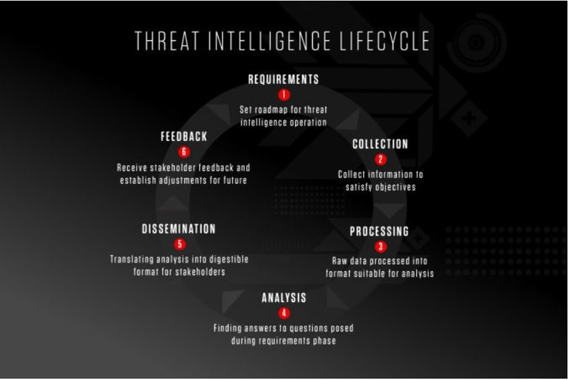
- Analysis
Now that all data are processed, the analyst team will make a drive to hunt potential security issues. The team will also decipher the dataset into actionable items and prepare it for stakeholders with valuable recommendations.
Admittedly, depending on the intended audience and objectives, threat intelligence can take many forms—from simple threat lists to peer-reviewed reports. Nevertheless, the goal of the analysis should be to make it understandable to the audience.
- Dissemination
The outcome of the analysis should now be distributed to its intended customers at the right time. Depending on the audience understanding level, the presentation of the analysis may vary but it should be concise & without too much technical jargons—ideally in a one-page report or a brief slide deck.
- Feedback
The final stage involves receiving feedback on the disseminated report from the stakeholders. Stakeholders will review the report and identify if their objectives are fulfilled. They may suggest changes to their priorities or the cadence at which they want to receive the intelligence report.


 714-333-9620
714-333-9620