Any modern cyber security organization, and even generally an organization that has a solid cyber security infrastructure, will be using the red team and blue team model to improve their digital security.
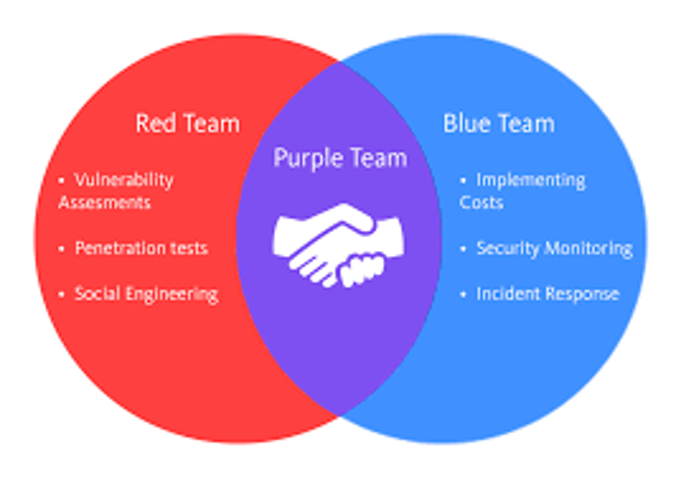
Red Teams
The red team is given the responsibility of penetrating the digital infrastructure by any means necessary. They aim to uncover the weaknesses brought about by the people, the processes, or the technology that is being used. On the other hand, the blue team is given the responsibility of securing the infrastructure using various strategies, technologies, and tactics. Essentially they are simulating a real-world situation in a controlled sandbox environment.
For the red team, the aim is to identify the weak areas in a system and highlight them. To do this, they will rely on a combination of penetration testing, vulnerability assessments, and cyber-attack simulations. It's very possible that the red team isn't successful in penetrating a system but this doesn't mean that the system is secure and doesn't need more work on it. The red team may have failed in their approach or even multiple approaches, but the real-world attacker may take a completely different route and be successful in penetrating that very system. For this reason, red team players need to stay updated with the latest trends in black hat hacking and also need to think like a real-world attacker would approach a problem. They are given specific targets such as trying to extract a certain kind of data, penetrate a database in a certain way, or any other objective. This is why the red team takes a certain approach and a strategy rather than just trying the first thing that comes to their head.
Blue Teams
On the other hand, we have the blue team who relies not only on the red teams' input but also on a lot of data coming in from a lot of other sources. Not only do they need the data, but they need the data very quickly, possibly in real-time, to make the adjustments necessary as soon as they are needed. This is why blue teams rely on a lot of AI, virtual assets, and live streams of data to stay on top of the digital environment that they are protecting. Moreover, blue teams can often be faced with multiple threats and attacks at a time so they need to be prepared to manage the situation as quickly as possible.
However, some organizations don't always have both teams and maybe relying on the work of either a red or a blue team. Larger organizations that can afford both teams may still not be making the most of the situation if they are using smaller teams. In reality, there is no limit to how small or large a cyber-defense operation can be, it's all about what's possible with the given resources.
Purple Teams
This is where purple teams come into play and create a more advanced cyber threat detection and prevention solution. Through the purple team solution both the red and blue teams are working in synergy rather than in isolation and results from either team are constantly relayed to the other team. This gives the organization a more holistic view of what is happening in response to a certain move that they make. Moreover, it also helps improve things such as threat hunting, network monitoring, and vulnerability detection.
The purple team still performs the function that would otherwise be done by the red or the blue team but the main difference is that it does that in a way where the effects are seen in real-time. This means that they can learn from each other more effectively and start coming up with unique solutions. Overall, this means purple teams help the organization to more efficiently combat cyber threats and improve digital defense systems.


 714-333-9620
714-333-9620